
In airports, shopping malls, or hotels, public charging stations can feel like a lifeline when your phone battery is nearly dead. But convenience comes with hidden risks: juice jacking, a cyberattack that could compromise your device’s data or infect it with malware. Drawing on exclusive insights from cybersecurity experts and years of research into charging security, this blog exposes how juice jacking works and delivers actionable tips to keep your devices safe.
Table of Contents
Part 1. What Is Juice Jacking?
Juice jacking is a cyberattack where hackers exploit USB ports at public charging stations to steal data or install malicious software. By tampering with charging stations or cables, attackers can harvest sensitive information like passwords, contacts, emails, or banking details. This attack capitalizes on the dual functionality of USB ports—transferring both power and data—creating a gateway for cybercriminals.
Part 2. How Juice Jacking Works
To expose the mechanics of juice jacking in vivid detail, cybersecurity expert Stickley orchestrated a controlled experiment along San Diego’s bustling waterfront. He built a modified charging station embedded with malware that mimics the hacking tools used by cybercriminals. To ensure ethical transparency, Stickley partnered with NBC News journalist Vicky Nguyen, who volunteered as a “controlled test subject.”
The moment Nguyen connected her phone to the rigged station, Stickley’s remote monitoring system sprang to life. Through a covert connection, he accessed her device in real time, mirroring her screen to a hidden dashboard. As she casually entered a credit card number to test an online purchase, every keystroke flashed across Stickley’s display—proof of how effortlessly sensitive data could be siphoned.
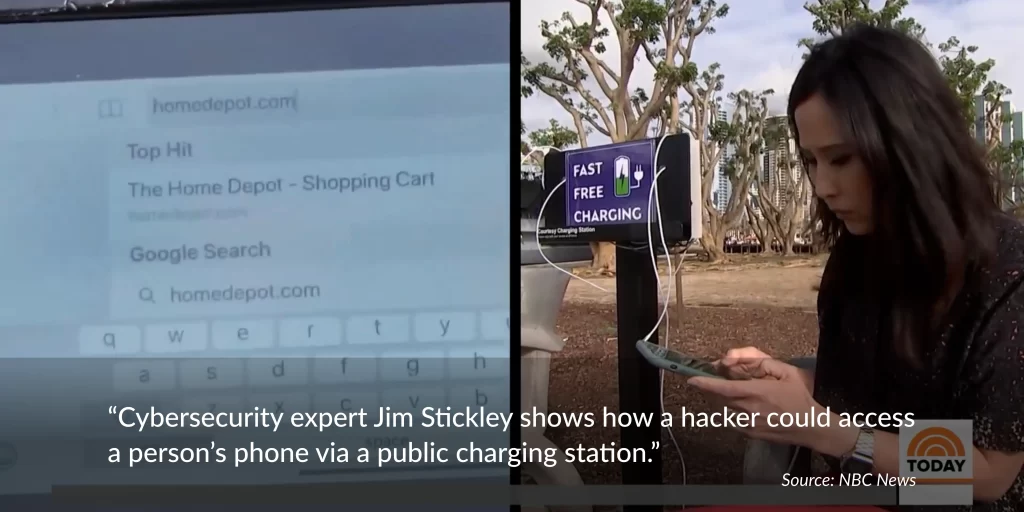
Over the next four hours, over 20 passersby—tourists, commuters, and business travelers—plugged into the compromised station. None noticed anything amiss. The station’s exterior showed no visible tampering, and its USB ports appeared identical to legitimate ones. Interviews afterward revealed most users assumed public charging stations were as safe as wall outlets. “I just needed a quick boost,” one participant admitted. “I didn’t even think about security.”
This experiment, later featured in an NBC News investigation, highlights two critical vulnerabilities:
1. Hardware Deception: Attackers can modify charging stations or cables to include malicious firmware, often undetectable to the naked eye.
2. User Trust Gap: Most people prioritize convenience over security, ignoring warnings about “Trust This Computer” prompts or unfamiliar hardware.
Stickley’s setup exploited the USB protocol’s default behavior—automatically initiating data handshakes unless explicitly blocked. Even devices set to “charge only” can sometimes fall victim to advanced exploits, especially when paired with compromised cables.
Part 3. How to Protect Your Phone
1. Use Your Own Charging Gear
The simplest defense? Avoid public stations altogether. Carry your own charger or trusted power bank to eliminate the risk entirely.
2. Use Charge-Only USB Cables
If you must use a shared station, opt for a charge-only cable. These cables disable data transfer, allowing power to flow while blocking hackers from accessing your device.
3. Deploy a USB Data Blocker
For added security, plug a data blocker into the charging port before connecting your cable. These compact devices disable the data pins in USB cables, ensuring only power passes through—no need to guess which cables are safe.
4. Inspect the Charging Station First
Check for signs of tampering: mismatched cables, loose parts, or unbranded hardware. Stick to reputable stations in secure locations, and treat free charging stations in random spots with the same skepticism as public Wi-Fi.
5. Never Trust “This Computer” Alerts
Modern smartphones prompt users to authorize data-sharing with connected devices. If your phone asks whether to “Trust This Computer” or “Allow Data Transfer” at a public station, unplug immediately. This is a glaring red flag for juice jacking.

Part 4. Choose Secure Charging: Meet HeyCharge
If you’re considering installing a commercial shared charging solution, why not choose HeyCharge? From factory production to assembly and delivery, every step of our process follows rigorous quality control protocols to ensure unmatched security. Here’s how we safeguard your charging experience:
1. Data-Free Charging: Our stations deliver power only—no data transfer capabilities exist, eliminating the risk of digital eavesdropping.
2. Certified Cables: We provide high-quality, tamper-resistant cables that are securely anchored and tested for safety and reliability.
3. Advanced Encryption: Our systems employ cutting-edge security protocols to block unauthorized access and firmware tampering.
4. Real-Time Monitoring: Our smart backend tracks every shared power bank’s status. If a unit is forcibly removed or goes missing, instant alerts notify site managers and block the compromised unit from future rentals.

Stay Safe, Stay Charged
Juice jacking is a silent threat lurking in public spaces, but awareness and proactive measures can keep your data secure. By using trusted gear, inspecting stations, and heeding device warnings, you minimize risks significantly. For businesses and venues seeking a secure charging partner, HeyCharge stands as the gold standard—combining military-grade security with seamless convenience.



